Staying Safe Online: 7 Essential Things You Should Know
Cyta’s Cybersecurity Centre presents the key principles for protecting yourself against Internet risks and threats
What you need to know:
Stay alert, investigate the validity of any information you find online and check anything that is unusual, unexpected or simply too good to be true.
1. Fake websites with malicious software
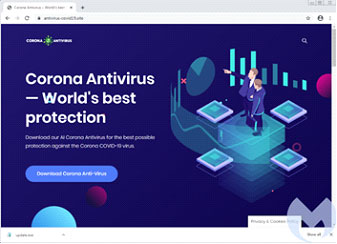
There are many examples like the one below, promoting free downloads of what is claimed to be the best antivirus for computers when, in fact, it contains embedded Remote Access Trojan software, enabling hackers to access your computer.
2. Phishing
Phishing attacks are always adapting to circumstances. For example, these days you may receive an e-mail claiming to be from a hospital and informing you that you have been exposed to COVID-19 through contact. You will be told to arrange a test once you have completed the attached form. When you open the document, your computer becomes infected with malicious software.
3. Attacks via VPN and teleworkers
The use of VPN connections by companies has attracted the attention of hackers who have intensified their attacks with the aim of discovering vulnerabilities that will give them access to corporate networks. At the same time, they are using Social Engineering and approaching teleworkers with supposed technical support or software updates in order to mislead them into revealing passwords or to gain access to the company’s computer.
4. Collaboration tools
The increased use of collaboration tools has led to them being targeted by individuals wishing to use them with malicious intent. The best-known example is Zoom, in which many software vulnerabilities have been identified that enable the theft of users’ e-mail addresses and photos, the sharing of malicious links, the sending of information to social networks (e.g. Facebook) without the users’ knowledge and even the theft of usernames and passwords from connected computers.
5. Product sales
Sales of masks and hand sanitizer, and even pharmaceuticals, are now the focus of many consumers’ online purchases, and this has led to the emergence of many new Internet stores that appear to be legitimate businesses but, in reality, they receive orders/payments worth millions of euros, without ever delivering the goods. Interpol recently uncovered such a European operation, which received €6.6 million worth of orders and then disappeared.

6. DNS Hijacking
By altering the addresses of the Domain Name Server (DNS), which converts names/domains into IP addresses, either through your modem or computer, hackers can re-route your computer traffic to malicious websites. They can then use such sites to spread fake news or to steal your data.
7. Other attacks
Ransomware attacks continue to be among the greatest dangers at this point in time. The rushed or mistaken opening of an e-mail attachment can put an entire organization out of action, locking every file on every connected computer and deny access until a ransom is paid.
Fake news is a huge problem around the world these days, impacting citizens’ effective communication and their ability to be properly informed.
12 Rules for Online Protection
- Install antivirus software and update it regularly.
- Install updates to your operating system and software as soon as they are available.
- Don’t visit websites that strangers suggest or are promoted on social media. Aimless browsing on your company computer should be avoided.
- Don’t reply to e-mails asking for personal information (phishing emails) and don’t open attachments to e-mails if you are not absolutely sure who has sent them.
- Protect your computer with strong passwords of at least 12 characters, using a combination of letters, numbers and symbols.
- Never share your passwords with anyone else.
- Only connect USBs that are used exclusively for work to your computer.
- Protect your home Wi-Fi network with a strong password.
- Don’t leave your computer unattended in open spaces.
- Don’t let other people use your company computer.
- Lock your desktop when you move away from your computer.
- Remote access to your corporate network should be via VPN, only through corporate computers and with two-factor authentication.